1. Deciding How much testing is enough should take into account :-i. Level of Risk including Technical and Business product and project risk
ii. Project constraints such as time and budget
iii. Size of Testing Team
iv. Size of the Development Teama) i,ii,iii are true and iv is false
b) i,,iv are true and ii is false
c) i,ii are true and iii,iv are false
d) ii,iii,iv are true and i is false
2. Test planning has which of the following major tasks?i. Determining the scope and risks, and identifying the objectives of testing.
ii.
Determining the test approach (techniques,test items, coverage,
identifying and interfacing the teams involved in testing , testware)
iii. Reviewing the Test Basis (such as requirements,architecture,design,interface)
iv. Determining the exit criteria.a) i,ii,iv are true and iii is false
b) i,,iv are true and ii is false
c) i,ii are true and iii,iv are false
d) ii,iii,iv are true and i is false
3. Evaluating testability of the requirements and system are a part of which phase:-a) Test Analysis and Design
b) Test Planning and control
c) Test Implementation and execution
d) Evaluating exit criteria and reporting
4.
One of the fields on a form contains a text box which accepts alphabets
in lower or upper case. Indentify the invalid Equivalance class value.a. CLASS
b. cLASS
c. CLass
d. CLa01ss
5. In a system designed to work out the tax to be paid:
An
employee has £4000 of salary tax free. The next £1500 is taxed at 10%
The next £28000 is taxed at 22% Any further amount is taxed at 40%
Which of these groups of numbers would fall into the same equivalence
class?a) £4800; £14000; £28000
b) £5200; £5500; £28000
c) £28001; £32000; £35000
d) £5800; £28000; £32000
6. Which of the following has highest level of independence in which test cases are :a) Designed by persons who write the software under test
b) Designed by a person from a different section
c) Designed by a person from a different organization
d) Designed by another person
7. We use the output of the requirement analysis, the requirement specification as the input for writing :-a) User Acceptance Test Cases
b) Integration Level Test Cases
c) Unit Level Test Cases
d) Program specifications
8. Validation involves which of the followingi. Helps to check the Quality of the Built Product
ii. Helps to check that we have built the right product.
iii. Helps in developing the product
iv. Monitoring tool wastage and obsoleteness.a) Options i,ii,iii,iv are true.
b) ii is true and i,iii,iv are false
c) i,ii,iii are true and iv is false
d) iii is true and i,ii,iv are false.
9. Which of the following uses Impact Analysis most?a) Component testing
b) Non-functional system testing
c) User acceptance testing
d) Maintenance testing
10. What is the expected result for each of the following test cases?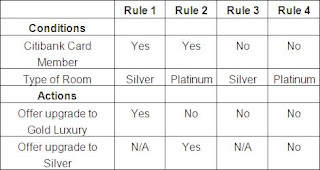
A. Citibank card member, holding a Silver room
B. Non Citibank-member, holding a Platinum room
a) A – Don’t offer any upgrade, B – Don’t offer any upgrade.
b) A – Don’t offer any upgrade, B – Offer upgrade to Gold.
c) A – Offer upgrade to Silver, B – Offer upgrade to Silver.
d) A – Offer upgrade to Gold, B – Don’t offer any upgrade.
11.
Repeated Testing of an already tested program, after modification, to
discover any defects introduced or uncovered as a result of the changes
in the software being tested or in another related or unrelated
software component:a) Re Testing .
b) Confirmation Testing
c) Regression Testing
d) Negative Testing
12. Impact Analysis helps to decide :-a) How much regression testing should be done.
b) Exit Criteria
c) How many more test cases need to written.
d) Different Tools to perform Regression Testing
13. Functional system testing is:a) testing that the system functions with other systems
b) testing that the components that comprise the system function together
c) testing the end to end functionality of the system as a whole
d) testing the system performs functions within specified response times
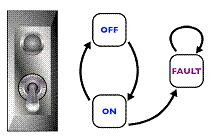 14. Consider the above state transition diagram of a switch.
14. Consider the above state transition diagram of a switch.
Which of the following represents an invalid state transition?a) OFF to ON
b) ON to OFF
c) FAULT to ON
15. Peer Reviews are also called as :-a) Inspection
b) Walkthrough
c) Technical Review
d) Formal Review
16. Consider the following statements:
i. 100% statement coverage guarantees 100% branch coverage.
ii. 100% branch coverage guarantees 100% statement coverage.
iii. 100% branch coverage guarantees 100% decision coverage.
iv. 100% decision coverage guarantees 100% branch coverage.
v. 100% statement coverage guarantees 100% decision coverage.a) ii is True; i, iii, iv & v are False
b) i & v are True; ii, iii & iv are False
c) ii & iii are True; i, iv & v are False
d) ii, iii & iv are True; i & v are False
17. The Kick Off phase of a formal review includes the following :-a) Explaining the objective
b) Fixing defects found typically done by author
c) Follow up
d) Individual Meeting preparations
18. Match every stage of the software Development Life cycle with the Testing Life cycle:i. Hi-level design a Unit tests
ii. Code b Acceptance tests
iii. Low-level design c System tests
iv. Business requirements d Integration testsa) i-d , ii-a , iii-c , iv-b
b) i-c , ii-d , iii-a , iv-b
c) i-b , ii-a , iii-d , iv-c
d) i-c , ii-a , iii-d , iv-b
19. Which of the following is not phase of the Fundamental Test Process?a) Test Planning and Control
b) Test implementation and Execution
c) Requirement Analysis
d) Evaluating Exit criteria and reporting
20. Which of the following techniques is NOT a black box technique?a) State transition testing
b) LCSAJ (Linear Code Sequence and Jump)
c) syntax testing
d) boundary value analysis
21. Success Factors for a review include :i. Each Review does not have a predefined objective
ii. Defects found are welcomed and expressed objectively
iii. Management supports a good review process.
iv. There is an emphasis on learning and process improvement.a) ii,iii,iv are correct and i is incorrect
b) iii , i , iv is correct and ii is incorrect
c) i , iii , iv , ii is in correct
d) ii is correct
22. Defects discovered by static analysis tools include :i. Variables that are never used.
ii. Security vulnerabilities.
iii. Programming Standard Violations
iv. Uncalled functions and proceduresa) i , ii,iii,iv is correct
b) iii ,is correct I,ii,iv are incorrect.
c) i ,ii, iii and iv are incorrect
d) iv, ii is correct
23. Test Conditions are derived from :-a) Specifications
b) Test Cases
c) Test Data
d) Test Design
24. Which of the following is true about White and Black Box Testing Technique:-a) Equivalance partitioning, Decision Table and Control flow are White box Testing Techniques.
b) Equivalence partitioning , Boundary Value Analysis , Data Flow are Black Box Testing Techniques.
c) Equivalence partitioning , State Transition , Use Case Testing are black box Testing Techniques.
d) Equivalence Partioning , State Transition , Use Case Testing and Decision Table are White Box Testing Techniques.
25. Regression testing should be performed:i. every week
ii. after the software has changed
iii. as often as possible
iv. when the environment has changed
v. when the project manager saysa) i & ii are true, iii, iv & v are false
b) ii, iii & iv are true, i & v are false
c) ii & iv are true, i, iii & v are false
d) ii is true, i, iii, iv & v are false
26. Benefits of Independent Testinga) Independent testers are much more qualified than Developers
b) Independent testers see other and different defects and are unbiased.
c) Independent Testers cannot identify defects.
d) Independent Testers can test better than developers
27. Minimum Tests Required for Statement Coverage and Branch Coverage :-Read P
Read Q
If p+q > 100 then
Print “Large”
End if
If p > 50 then
Print “pLarge”
End ifa) Statement coverage is 2, Branch Coverage is 2
b) Statement coverage is 3 and branch coverage is 2
c) Statement coverage is 1 and branch coverage is 2
d) Statement Coverage is 4 and Branch coverage is 2
28. Minimum Test Required for Statement Coverage :-Disc = 0
Order-qty = 0
Read Order-qty
If Order-qty >=20 then
Disc = 0.05
If Order-qty >=100 then
Disc =0.1
End if
End ifa) Statement coverage is 4
b) Statement coverage is 1
c) Statement coverage is 3
d) Statement Coverage is 2
29. The structure of an incident report is covered in the Standard for Software Test Documentation IEEE 829 and is called as : -a) Anomaly Report
b) Defect Report
c) Test Defect Report
d) Test Incident Report
30. Which of the following is the task of a Test Lead / Leader.i. Interaction with the Test Tool Vendor to identify best ways to leverage test tool on the project.
ii. Write Test Summary Reports based on the information gathered during testing
iii. Decide what should be automated , to what degree and how.
iv. Create the Test Specificationsa) i, ii, iii is true and iv is false
b) ii,iii,iv is true and i is false
c) i is true and ii,iii,iv are false
d) iii and iv is correct and i and ii are incorrect
31. Features of White Box Testing Technique :-i. We use explicit knowledge of the internal workings of the item being tested to select the test data.
ii.
Uses specific knowledge of programming code to examine outputs and
assumes that the tester knows the path of logic in a unit or a program.
iii. Checking for the performance of the application
iv. Also checks for functionality.a) i, ii are true and iii and iv are false
b) iii is true and i,ii, iv are false
c) ii ,iii is true and i,iv is false
d) iii and iv are true and i,ii are false
32. Which of the following is a part of Test Closure Activities?i. Checking which planned deliverables have been delivered
ii. Defect report analysis.
iii. Finalizing and archiving testware.
iv. Analyzing lessons.a) i , ii , iv are true and iii is false
b) i , ii , iii are true and iv is false
c) i , iii , iv are true and ii is false
d) All of above are true
33. Which of the following will be the best definition for Testing :-a) The goal / purpose of testing is to demonstrate that the program works.
b) The purpose of testing is to demonstrate that the program is defect free.
c) The purpose of testing is to demonstrate that the program does what it is supposed to do.
d) Testing is executing Software for the purpose of finding defects.
34. Which of the following is not a type of incremental testing approach?a) Top down
b) Big-bang
c) Bottom up
d) Functional incrementation.
35. Drivers are also known as:i. Spade
ii. Test harness
iii. Scaffoldinga) i , ii are true and iii is false
b) i , iii are true and ii is false
c) ii , iii are true and i is false
d) All of the above are true
36. Exit Criteria may consist of :-i. Thoroughness measures , such as coverage of code, functionality or risk
ii. Estimates of Defect density or reliability measures.
iii. Residual risk such as defects not fixed or lack of test coverage in certain areas
iv. Verifying the Test Environment.a) iv is correct and i,ii,iii are incorrect.
b) i,ii,iii is correct and iv is incorrect
c) ii is correct and i,ii,iii are incorrect
d) iii and iv are correct and i,ii are incorrect
37. Which of the following helps in monitoring the Test Progress:-i. Percentage of Test Case Execution
ii. Percentage of work done in test environment preparation.
iii. Defect Information e.g. defect density, defects found and fixed
iv. The size of the testing Team and skills of the engineersa) iv is correct and i,ii,iii are incorrect
b) i,ii,iii are correct and iv is incorrect
c) i,ii are correct and iii,iv are incorrect
d) i,iv are correct and ii , iii are incorrect
38. The selection of a test approach should consider the context :-i. Risk of Failure of the Project, hazards to the product and risks of product failure to humans
ii. Skills and experience of the people in the proposed technique, tools and methods
iii. The objective of the testing endeavor and the mission of the testing team.
iv. The size of the testing Teama) i,ii,iii,iv are true
b) i,ii,iii are true and iv is false.
c) ii,iii,iv are true and i is false.
d) i,iv are true and ii, iii are false.
39. In case of Large Systems :-a) Only few tests should be run
b) Testing should be on the basis of Risk
c) Only Good Test Cases should be executed.
d) Test Cases written by good test engineers should be executed.
40. The Provision and Management of a controlled library containing all the configurations items is called asa) Configuration Control
b) Status Accounting
c) Configuration Identification
d) Configuration Identification
Answers :
1 c
2 a
3 a
4 d
5 d
6 c
7 a
8 b
9 d
10 d
11 c
12 a
13 c
14 c
15 c
16 d
17 a
18 d
19 c
20 b
21 a
22 a
23 a
24 c
25 c
26 b
27 c
28 b
29 a
30 a
31 a
32 c
33 d
34 b
35 c
36 b
37 b
38 b
39 b
40 a

 Active Topics
Active Topics  Memberlist
Memberlist  Calendar
Calendar  Search
Search 
 Active Topics
Active Topics  Memberlist
Memberlist  Calendar
Calendar  Search
Search 



 Topic: ISTQB Sample Question Paper #9
Topic: ISTQB Sample Question Paper #9 IP Logged
IP Logged

